Cloud Integration on Neo does not (yet) have an end of life, but SAP is now only delivering new integration tenants on Cloud Foundry. SAP would prefer all clients to migrate to Cloud Foundry as soon as possible. Also, going forward, new features will be delivered first in Cloud Foundry environments, so now is a good time to get started with Cloud Foundry.
In a Neo Environment, it was possible to consume an integration flow (iFlow) using Basic Authentication with a SAP S- or P-user. This user needed to be provided with the necessary predefined role ‘ESBMessaging.send’ or a user-defined role with the role being assigned to the iFlow. Configuration appeared as follows:
In a Cloud Foundry Environment, this has changed. The preferred authentication methods are now Client Certificates or OAUTH2 tokens. While Basic Authentication remains possible, this is no longer recommended for production use. Moreover, using a S- or P-user will no longer work. Instead, you will need to generate credentials in a Cloud Foundry service instance.
Nonetheless, there are instances in which you may want to use Basic Authentication. Perhaps you need to run a test from an API test tool. Or perhaps you just need something short-term that is more simple than the recommended methods. This blog will explain the steps necessary to generate and use the credentials required for a Cloud Foundry service instance. Let’s get started!
Related References: https://help.sap.com/docs/CLOU...
Secure iFlow with User Role authorization
Optional: Create user-defined role
It is possible to secure an integration flow with a user-defined role instead of using the predefined ESBMessaging.send role. The following explains how.
In the Cloud Foundry environment, a monitor exists in the Cloud Integration monitoring to maintain user roles.
Open the ‘User Role’ monitor in the ‘Manage Security’ section in the ‘Monitoring’ section in the Cloud Integration tenant.
Create a new role by selecting the ‘Add’ option.
In the creation dialog, enter the ‘Role Name’ and a ‘Role Description’.
This will result in the following.
Configure Sender Channel Authorization Option
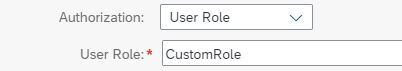
Next, you must configure ‘User Role’ as the authorization option in the sender channel in the integration flow.
The default role provided by SAP is ESBMessaging.send. This role can be used if no additional integration flow-specific authorization checks are needed. If only specific users should be allowed to send messages to this integration flow, you can enter your own role. (See above how to create this custom role).
Create Service Instance and Service Key
With a service instance, you define how to access a certain SAP Business Technology Platform (BTP) service.
In the context of SAP Cloud Integration, a service instance is the definition of an OAuth client.
However, during runtime, no access token is retrieved from the token server. Instead of an access token, the
‘clientid’ and ‘clientsecret’ values from the service key are used as the user credentials to access the integration flow endpoint.
As a pre-requisite, make sure your sub-account is entitled to Process Integration Runtime, as follows:
And that your sub-account has Cloud Foundry enabled, and a space created:
Now you can create the a new Service Instance in the SAP BTP Cockpit: Services -> Instance and Subscriptions -> Create
For the required basic info, provide the following information:
- Service: Process Integration Runtime
- Plan: Integration-flow (API is also possible if you want to create client credentials for API management instead of Cloud Integration).
- Runtime Environment: Cloud Foundry
- Space: Select your created Cloud Foundry space (for example DEV)
- Instance Name: Provide a CLI-friendly name for the service instance
Note: SAP recommends using a CLI-friendly name to enable managing your instances with the SAP BTP command line interface as well. A CLI-friendly name is a short string (up to 32 characters) that only contains alphanumeric characters (A-Z, a-z, 0-9), periods, underscores, and hyphens. Your instance name can't contain white spaces if you want your instance name to be CLI-friendly.
For the instance parameters, provide the following information:
- Grant-Type: Client Credentials
- Roles: Either use the pre-defined standard role ESBMessaging.send or replace it with your own user-defined role:
Note: There is no drop-down selection possible for ‘Roles’. You must use exactly the same name as was created earlier in the User Role monitor!
Next step is to create a service key by selecting the instance. Under ‘Service Keys’, press ‘Create’:
Provide a ‘Service Key Name’ and for ‘Key Type’ select ‘ClientID/Secret’.
I recommend providing a meaningful name here. For example, you could include the external party with whom you will share these authentication credentials. This will help you to easily determine the purpose of these keys later on.
Once the service key is created (it can take some minutes), press the ‘View Credentials’ button and you will be able to retrieve the generated ‘clientid’ & ‘clientsecret’ that can be used for authentication.
‘clientid’ corresponds to the basic authentication username and ‘clientsecret’ to the password.
Here are example Basic Authorization details to use in SOAPUI :
Note: You should create a service instance per (user-defined) Authorization Role.
For each service instance, you can create multiple service keys, allowing you to secure an iFlow with a specific user role and create several basic authentication secrets which you can share with the iFlow consumers.
Conclusion
And that’s it! You should now be able to successfully generate and use Basic Authentication credentials for inbound communication when using SAP Cloud Integration in the Cloud Foundry environment. While Client Certificates or OAUTH2 tokens are now the methods of authentication recommended by SAP, Basic Authentication can still be useful… as, I hope, was this article!